1.4 Multiple Access - Why and How
A key property of wireless networking is that it is fundamentally a
broadcast technique, i.e.,
- Number of receiving users is usually multiple and unknown
- Received power is usually unknown
In this topic, we discuss the fundamentals of multiple access techniques.
First, we take a quick look at wireless network topologies. Then we consider how
to divide the channel resource into chunks that can be allocated for
communications, and, finally, how the chunks are assigned to users.
Wireless Network Topologies
Common topologies:
- 1. Centralized (star, client-server)
- 2. Distributed (peer-to-peer)
- 3. Multi-hop
Centralized Topology
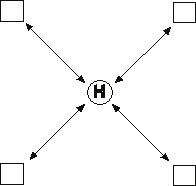
All Communication goes through the hub
Centralized Topology -- Characteristics
- Simplest and most popular
- Easy connection to other networks (centralized gateway)
- Simple network access and control mechanisms (power control,
synchronization)
- Mobile coverage is extended via hub retransmission
- Minimum two-hop delay
- Single failure point
Distributed Topology
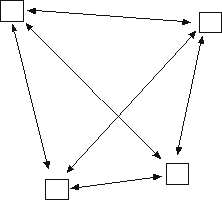
All nodes communicate directly with one another
Distributed Topology -- Characteristics
- No easy (centralized) methods for network control
- Must designate server for gateway
- Fast connectivity (need not register with hub)
- Coverage limited by mobile transmit power
- Minimum delay of one hop
- No single failure point
Multi-Hop Topology
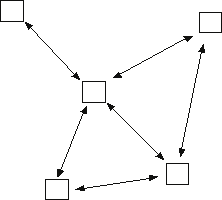
Generalization of distributed topology -- multiple hops possible
Multi-Hop Topology -- Characteristics
- Good redundancy and reliability (multiple paths)
- Requires complex message routing, flow control algorithms
- Possible high delays
- Complex - currently in use in military networks
Multiple Access Methods
Concept: In wireless networks, the channel resource must be shared among
multiple users.
Two considerations:
-- How to split up the channel resource (multiple access method)
-- How to allocate the pieces (assignment strategy)
The channel can be divided up according to time, frequency band, or both.
Multiple Access Methods - Types
- Time domain -- TDMA (Time-Division Multiple Access)
- Frequency domain -- FDMA (Frequency-Division Multiple Access)
- Hybrid (FDMA/TDMA)
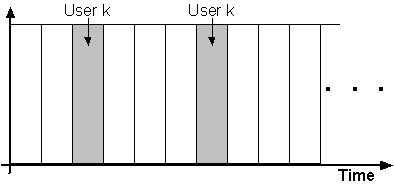
FDMA
The classic approach - divides the frequency spectrum into channels.
Frequency
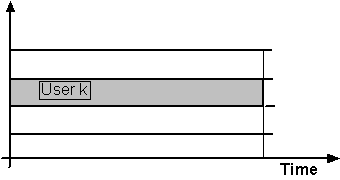
TDMA
Divides time into slots (time intervals)
Frequency
Other Methods
Hybrid FDMA/TDMA - divides time-frequency plane into ``blocks'' rather than
``strips''
Frequency
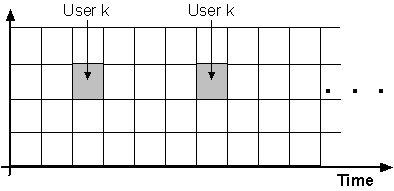
There is another possibility in which the time-frequency is shared by all
users simultaneously:
-
- Signals are differentiated by cross-correlation properties
- These properties come from using certain signature sequences
or spreading codes.
- This method is known as CDMA (Code-Division Multiple Access).
- Hybrid TDMA/FDMA/CDMA methods can also be used.
Comparison of Multiple Access Methods
FDMA --
- simplest in principle; mature technology
- Requires strict frequency coordination
- must provide guard bands between channels to reduce adjacent-channel
interference
- requires complexity in RF section of radio due to multiplicity of carrier
frequencies
TDMA --
- well understood
- requires strict time coordination (synchronization)
- must provide guard time between time slots
- requires only one radio RF section -- all users share the same carrier
frequency
- more complicated baseband section of radio due to strict timing
requirement
CDMA --
- codes used to simultaneously spread information across frequency band
=> diversity advantage (fading/interference mitigation)
- most complex; developing technology
- little or no time/frequency coordination between users required
- DS requires only one radio RF section -- all users share the same carrier
frequency
- complexity carried in signature sequences and receiver processing
- has potential advantages for channels with multipath fading and
interference due to inherent time-frequency diversity
- easily exploits trunking efficiency
Assignment Strategies (Media Access Control)
Q: How to allocate the resource, i.e.,
- 1. frequency channels
- 2. time slots
- 3. spreading codes
- 4. combinations of the above?
5. to network users?
Remark: the protocols that implement the assignment strategies are known as
media access control (MAC) protocols.
Basic Concepts
Strategy can be based on
- reservation or
- contention;
are collisions (network conflicts) avoided, or
detected and then recovered from?
Strategy can be
- static (fixed) or
- dynamic;
is access unchanging or can it be modified in
response to changes in network traffic and loading?
I. Fixed (static) assignment -- each user gets a fixed portion of the
channel resource (permanent reservation) whether it needs it or not.
II. Demand assignment -- varied over time
- 1. Centralized - simple, non-robust
-
- (a) Polling
- (b) Reservation
2. Decentralized (distributed) -- complex, robust (e.g., token-based)
III. Random access -- users may transmit at any time, but the network
must correct errors due to collisions: i.e., there must be feedback to the
transmitters regarding the success of transmissions.
The fixed and demand assignment methods can be regarded as reservation-based
methods, while random access protocols are contention-based.
The choice between reservation and contention methods is often determined
primarily by network transmission delay:
- If relatively long, reservation-based methods are usually more efficient
- If relatively short, the simpler, more robust random access methods will
not suffer loss of efficiency due to transmission delays
Examples of Random-Access Methods
1. ALOHA -- users transmit whenever they have data, listen for collision, and
re-transmit after a random wait if necessary.
- 2. Slotted ALOHA -- users are time-synchronized to begin fixed-length
transmissions only at the beginning of periodic time slots. Thus
only type of collision is total.
-
3. CSMA (Carrier Sense Multiple Access) -- users listen to channel
and transmit only it is not being used. -
4. CSMA/CD (CSMA with Collision Detection) -- users listen while
transmitting. -
Remark: CSMA/CD may be subject to ``hidden terminal'' problem,
where a remote may not be within range of another transmitting
remote that is within range of the base station. Thus CSMA is
less suitable for centralized topologies.
5. DSMA (Data Sense Multiple Access) -- a hybrid scheme with both random access
and collision avoidance:
-
- hub transmits ``busy bit'' to let users know channel
state
- it channel is free, users transmit
- right away, or
- in one of several time slots selected
at random
- Users determine success of transmission by CD or acknowledgment
from destination user.
- Resolves ``hidden terminal'' problem in centralized
networks
Relationship of Topology to MAC Protocols
Natural fits:
distributed topology <--> contention-based protocols
centralized topology <--> reservation-based protocols



